Today, most cyber-attacks are carried out by exploiting existing vulnerabilities in the network. Yet, many organizations still rely on firewalls and antivirus tools to protect their environment and consider it good enough. The rise of sophisticated threats is outpacing the ability of most organizations to combat them, and the average attack now goes undetected for 78 days.
Successful and more rapid detection of advanced attacks requires a different approach, one that provides greater visibility and management along with a dynamic understanding of the ever-changing threat landscape.
Keeping pace with the daily grind of monitoring your network environments for attacks-in-motion can burnout the best of staff. As the alerts build and response is stretched thin, the protection your organization relies upon can become vulnerable to failure.
At Cyber1 Security, our network threat detection and response team deliver real-time intelligence and visibility into events occurring within your environment, regardless of whether it is a device, software application or server on its own data center or in a cloud environment. We provide rapid investigation and remediation—all managed 24/7 by Security Operations Center (SOC) staff skilled at quickly discerning what’s real from the white noise of false positives.
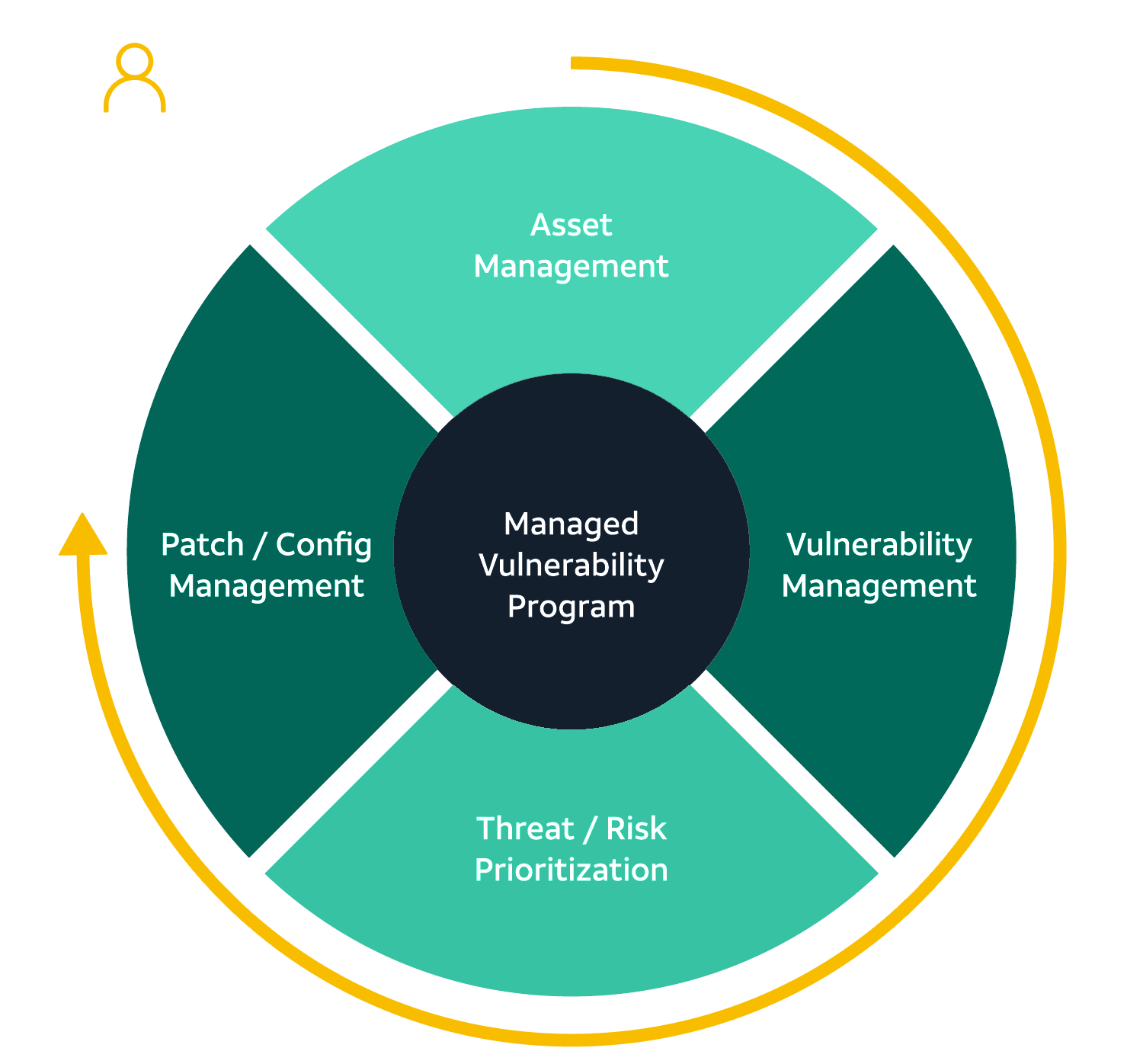
Vulnerability and threat management can dramatically improve cyber resilience by ensuring vulnerabilities are quickly identified, classified, and prioritized for remediation before attackers have an opportunity to exploit your weaknesses and act against you.
Our attack detection is nonlinear, imitating the ad-hoc way an attacker moves through a network. We rewind the cyber kill chain, automatically reevaluating security data and comparing it against newly gathered threat intelligence regarding attacker tactics, techniques, and procedures.
Cybercriminals don’t work normal hours. Attacks can hit at any time, and the Cyber1 SOC is ready when the time comes. We’re continuously monitoring, detecting, and remediating threats to keep your systems secure – chasing down the real threats from the noise and creating a force multiplier for your IT team who is now free to focus on your IT operations.
The Cyber1 SOC team includes certified security techs, including security analysts, incident response analysts, security researchers, and threat hunters. Do you already have a few security techs on staff? Our team will take care of alerting and triaging and consult your team when there are issues they need to handle.
The threat landscape is always changing. The Cyber1 Security Cyber Research Unit is dedicated to identifying the latest threats, ensuring our SOC team is on high alert to catch what’s lurking in the shadows. We provide you with prioritized reports and clear remediation guidance, so that you can keep one step ahead of cybercriminals.